JWT versus OAUTH versus API keys
Concept-focused guide for JWT versus OAUTH versus API keys, by the end of this article, you’ll be able to confidently choose the right authentication approach for various real-world scenarios
~8 min read
Overview
Welcome, architects and developers! Today we’re diving deep into the practical world of API authentication, focusing on JWT (JSON Web Tokens), OAuth 2.0, and API Keys. By the end of this article, you’ll be able to confidently choose the right authentication approach for various real-world scenarios, understand the strengths and weaknesses of each method, and recognize the subtle trade-offs involved in their design and implementation. This knowledge is crucial for anyone building secure, scalable APIs that serve mobile apps, web clients, or internal services.
Concept-by-Concept Deep Dive
1. Authentication Mechanisms: API Keys, JWT, and OAuth 2.0
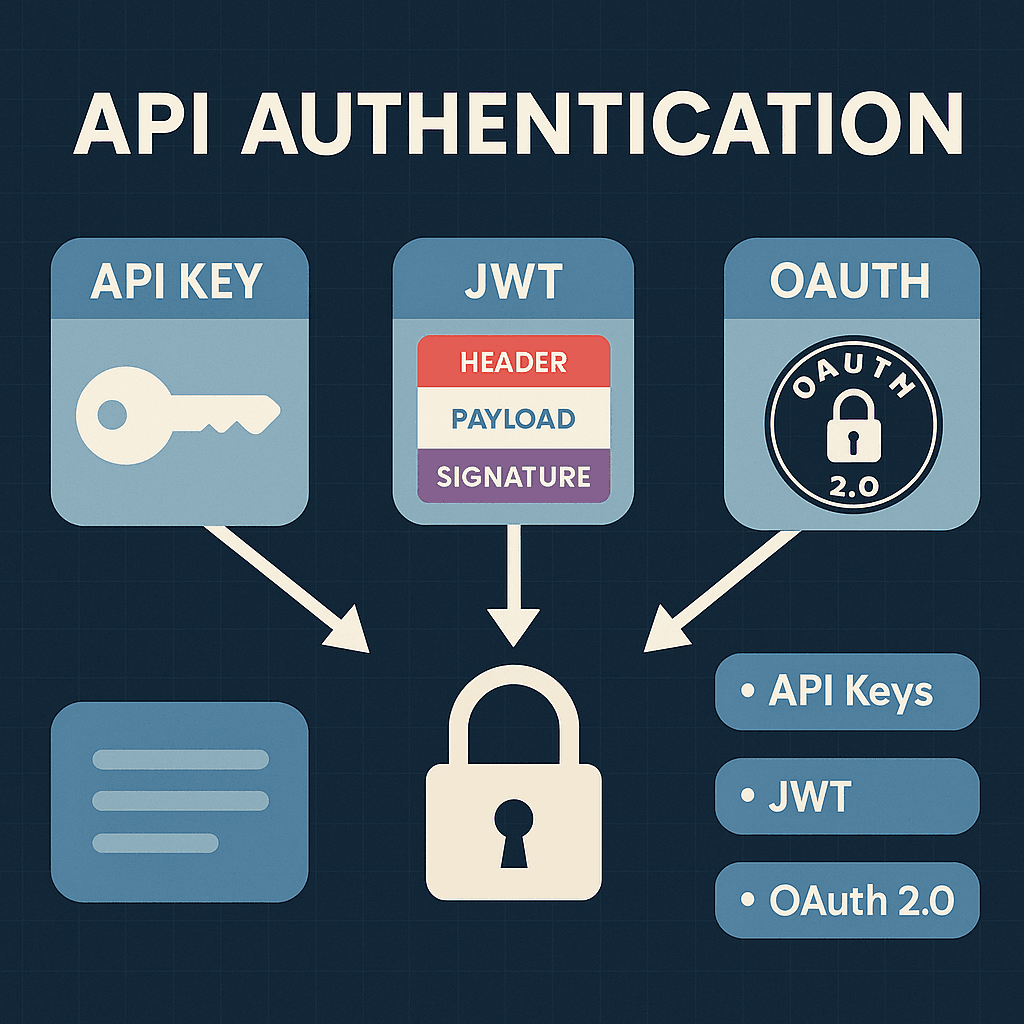
Authentication is the process of verifying who or what is accessing your API. The three most common mechanisms are API Keys, JWT, and OAuth 2.0, each serving different needs.
API Keys
- What Are API Keys?
Simple, static tokens (often random strings) that a client includes in requests, typically via headers or query parameters. They're used to identify the calling application, not the user. - Typical Use Cases:
Public APIs where you only want to track or limit usage per application (not per user), backend cron jobs, or basic internal service calls. - Limitations:
Cannot express user identity or permissions; hard to revoke; easily leaked if exposed in client code; no built-in expiry.
JWT (JSON Web Tokens)
- What Are JWTs?
Self-contained, signed tokens that can encode claims about a user or service, such as identity, roles, and expiry times. They are stateless—meaning the server doesn't need to keep session data. - Typical Use Cases:
Stateless authentication between microservices, fine-grained access control, and scalable session management for SPAs (Single Page Applications). - Components:
Header (metadata), Payload (claims), Signature (integrity check). - Strengths:
Easy to validate, portable, supports fine-grained claims, tamper-resistant if signed properly. - Weaknesses:
Hard to revoke before expiry unless paired with a revocation list; if mishandled, can leak sensitive info.
OAuth 2.0
- What Is OAuth 2.0?
An authorization framework for delegated access, enabling apps to act on a user's behalf without sharing passwords. It issues access tokens after a user grants consent. - Typical Use Cases:
When third-party applications need access to user data (e.g., social logins, integrations), or when you need robust scopes and consent. - Key Flows:
Authorization Code (web apps), Implicit (now discouraged), Client Credentials (machine-to-machine), and Resource Owner Password Credentials (legacy/rare). - Complexity:
More moving parts (authorization server, consent screens, token management) but also more flexibility and control.
Common Misconceptions
- API Key ≠ User Authentication:
Remember, API keys identify applications, not users. - JWT ≠ OAuth:
JWT is a token format; OAuth is a protocol. OAuth can issue JWTs, but not all JWTs are OAuth tokens. - OAuth is Not Overkill:
If you need delegated access or granular consent, OAuth is not overkill—it's best practice.
2. Stateless vs. Stateful Authentication
Stateless Authentication
- Definition:
All information needed to validate a request is contained in the token itself (e.g., JWT), so the server doesn't keep session state. - Benefits:
Scalability (no central session store), easier horizontal scaling, fast validation. - Drawbacks:
Token revocation is non-trivial; once issued, tokens are valid until expiry unless you check a blacklist.
Stateful Authentication
- Definition:
Server maintains session state or token validity (e.g., traditional session IDs, OAuth with refresh token blacklists). - Benefits:
Easy to invalidate sessions/tokens at any time. - Drawbacks:
Harder to scale, requires central session management.
Practical Trade-offs
- Use stateless tokens (JWT) for microservices where scaling and performance matter.
- Use stateful methods where immediate revocation or strict session control is necessary.
3. Fine-Grained Access Control and Auditing
- Why It Matters:
Modern APIs often need to distinguish between different types of actions (like "view" vs. "transfer money") and record who did what for compliance. - How JWT Helps:
JWTs can embed roles, permissions, and user IDs as claims, allowing backend services to enforce and audit fine-grained actions. - How OAuth Helps:
OAuth scopes can limit what a token can do (e.g., "read" vs. "write"), and consent records can be audited. - API Key Limitation:
API keys can't encode user identity or permissions, making auditing and fine-grained control difficult.
Common Misconceptions
- API Keys Are Not Sufficient for User-Level Permissions:
They can only identify the calling application, not the end-user performing an action. - Claims in JWT Must Be Verified:
Never trust claims unless you've validated the signature and checked expiry.
4.
🔒 Continue Reading with Premium
Unlock the full vlog content, professor narration, and all additional sections with a one-time premium upgrade.
One-time payment • Lifetime access • Support development
Join us to receive notifications about our new vlogs/quizzes by subscribing here!